Service Accounts How-to
Manage service accounts
Managing service accounts
Service accounts exist with defined permissions in a specific cluster and aren't associated with any user accounts.
Authorization tokens are the sole mechanism by which service accounts can gain access to a cluster.
This page describes how to create, manage, and delete service accounts and their corresponding auth tokens using both the Hydrolix UI and the Config API.
Service account overview
Service accounts are easy to create and delete.
Service accounts themselves exist at the global scope in a cluster. See Required permissions for users needing to manage service accounts.
Service accounts must be deleted as there is no way to disable a service account. Only user accounts can be disabled.
Service account token lifecycle
Tokens and their lifecycle have the following characteristics:
- Each service account can have unlimited valid tokens
- Tokens have a configurable lifetime, determined by the
expiryquery parameter - Tokens default to a one year lifetime, 365 days
- Tokens are valid until expiration, revocation, or deletion of the service account
- Token invalidation applies to all tokens associated with the service account
All tokens are invalidated
It's not possible to revoke a single token.
Required permissions
Users creating and managing service accounts must have the following permissions at the global scope:
add_serviceaccountdelete_serviceaccountview_serviceaccounttokens_serviceaccount
Additional permissions are required to define and manage roles. See the RBAC How-to.
Quick links
| Action | ||
|---|---|---|
| View a service account | view using UI | view using API |
| Create a service account | create using UI | create using API |
| Assign roles | assign using UI | assign using API |
| Generate a token | token using UI | token using API |
| Revoke tokens | revoke using UI | revoke using API |
| Delete a service account | delete using UI | delete using API |
Managing service accounts in the UI
View in UI
Users with the view_serviceaccount permissions can see all service accounts in the cluster.
Tokens are never viewable after generation whether sent to the API or UI. The user creating the token is responsible for secure management of the tokens.
- Log in to the portal.
- Click Security in the left sidebar.
- Click Service Accounts in the top bar.
From this page, use the vertical ellipsis (⋮) on each entry to Add Roles, Create token, or Delete account.
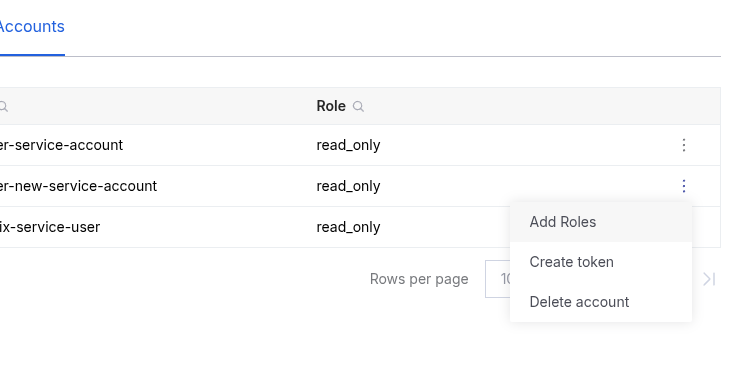
Create in UI
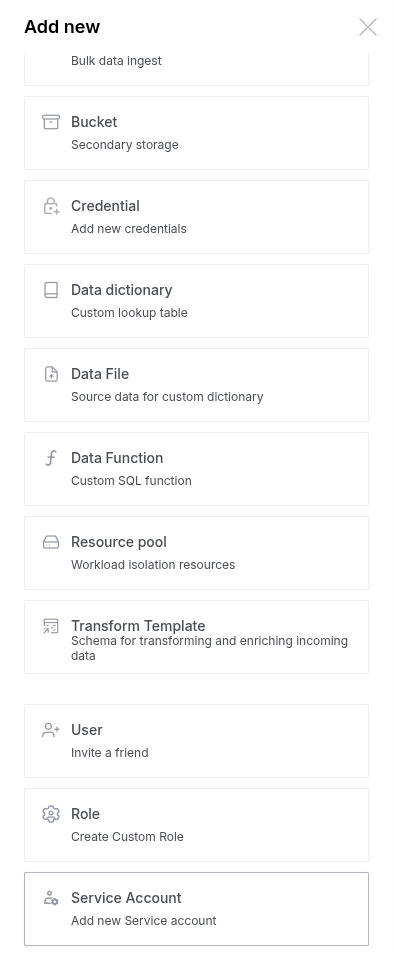
- In the top right corner of the screen, click the + Add new button.
- Select the Service Account option in the right sidebar.
- Enter a unique service account name.
- Click Create & Continue.
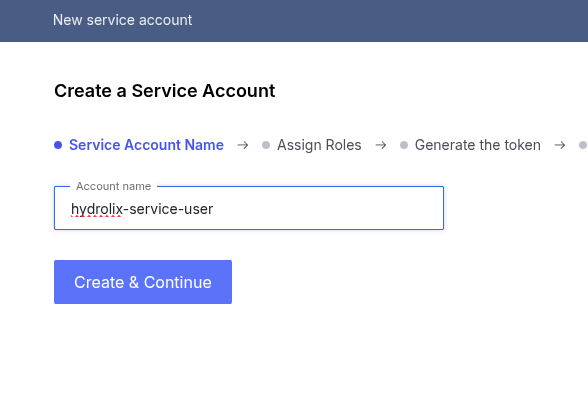
The two subsequent steps in the service account creation workflow support assignment of roles to the service account and generation of a first token. These steps can be skipped and completed later.
Assign roles in UI
By default a service account has no roles at creation. Users must have an initial role, but not service accounts. Use the account permissions (RBAC) system to group permissions into roles to be attached to service or user accounts.
- Log in to the portal.
- Click Security in the left sidebar.
- Click Service Accounts in the top bar.
- Use the vertical ellipsis (⋮) to select Add Roles.
- Enter all roles in the Select role multiselect drop-down.
- Click Assign roles.
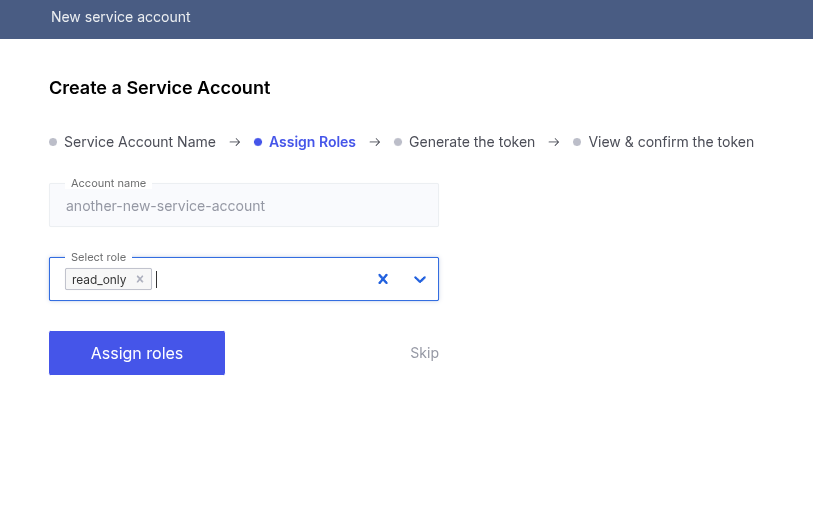
Role assignment occurs immediately. Since permissions are checked at time of use, subsequent requests will experience the new permissions.
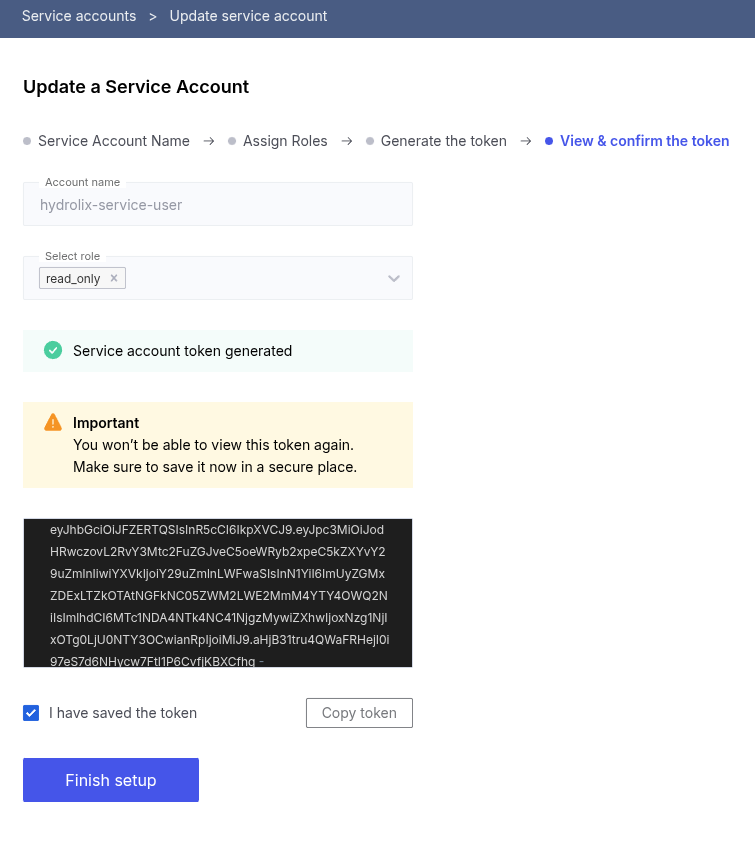
Generate token in UI
See Service account token lifecycle.
Token lifetime defaults to 365 days. It's not possible to set the expiry date and time using the UI. See also Generate token with API.
- Log in to the portal.
- Click Security in the left sidebar.
- Click Service Accounts in the top bar.
- Use the vertical ellipsis (⋮) to select Create token.
- Click Generate token.
- Collect and save the token somewhere safe. You won't be able to retrieve the token after leaving this page.
- Click checkbox for I have saved the token.
- Click Finish setup.
Revoke tokens in UI
It's not possible to revoke or invalidate all tokens associated with a service account with the UI.
Consider the following options:
- Revoke tokens with the API
- Create a new service account and token. Switch clients and applications. Delete the old service account
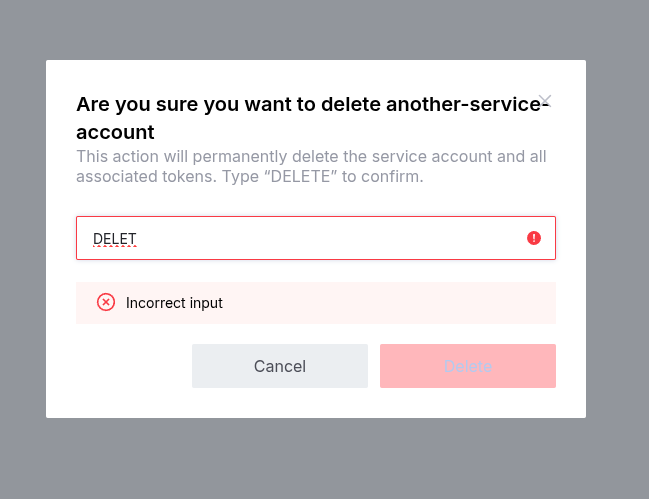
Delete in UI
- Log in to the portal.
- Click Security in the left sidebar.
- Click Service Accounts in the top bar.
- Use the vertical ellipsis (⋮) to select Delete account.
- Confirm the deletion of the service account by typing
DELETEin the dialog.
Managing service accounts with the API
Performing all of the actions against the Config API in these examples requires a valid user authorization token.
Common variables used in these examples
| Shell variable | Contents |
|---|---|
$HDX_HOSTNAME | The fully qualified domain name (FQDN) of the cluster |
$HDX_HYDROLIX_URL | The base URL of the cluster |
$HDX_USER | Username for authenticating to the API, to fetch an auth token |
$HDX_PASSWORD | Password for authenticating to the API, to fetch an auth token |
$HDX_TOKEN | A user token. User account must have service account permissions |
$HDX_SA_UUID | The service account UUID, needed for API calls operating on a specific service account |
$HDX_SERVICE_TOKEN | A service token returned in the response from the Create service account endpoint |
Obtain a user token to execute the examples below. See also Intro to Config API.
General workflow
- Acquire an auth token using Login to Hydrolix. See also acquiring auth tokens.
- Call Create service account with optional name and save the new UUID in the response.
- Assign roles to UUID with endpoint Add roles to user.
- Generate service account tokens.
- Invalidate service account tokens to block all access to the service account.
- Delete service account when the account is no longer needed.
Login to the API
Get the bearer token, which is good for the next 24 hours, to authenticate future API calls. This command assumes you've set the $HDX_HOSTNAME, $HDX_USER and $HDX_PASSWORD environment variables:
export HDX_TOKEN=$(
curl -v -X POST -H "Content-Type: application/json" \
https://$HDX_HOSTNAME/config/v1/login/ \
-d "{
\"username\":\"$HDX_USER\",
\"password\":\"$HDX_PASSWORD\"
}" | jq -r ".auth_token.access_token"
)
View with API
Show a single service account or list all.
List all service accounts
Use the endpoint List service accounts.
curl --fail \
--header "authorization: Bearer ${HDX_TOKEN}" \
--header "content-type: application/json" \
-- "${HDX_HYDROLIX_URL}/config/v1/service_accounts/"
{
"next": 0,
"previous": 0,
"current": 1,
"num_pages": 1,
"count": 2,
"results": [
{
"uuid": "097c6259-9787-4400-b54a-50ecdac36110",
"audit": true,
"is_service_account": true,
"name": "another-service-account"
},
{
"uuid": "e2dc1d11-6d90-4ad4-9ec6-a62c8a689d66",
"audit": true,
"is_service_account": true,
"name": "hydrolix-service-user"
}
]
}
Request a specific service account by its UUID
Use the endpoint Retrieve service account with the service account UUID in the URL.
HDX_SA_UUID=e2dc1d11-6d90-4ad4-9ec6-a62c8a689d66
curl --fail \
--header "authorization: Bearer ${HDX_TOKEN}" \
--header "content-type: application/json" \
-- "${HDX_HYDROLIX_URL}/config/v1/service_accounts/${HDX_SA_UUID}"
{
"uuid": "e2dc1d11-6d90-4ad4-9ec6-a62c8a689d66",
"audit": true,
"is_service_account": true,
"name": "hydrolix-service-user"
}
Create with API
The endpoint Create service account requires the name attribute in the POST body.
curl --fail \
--request POST \
--header "authorization: Bearer ${HDX_TOKEN}" \
--header "content-type: application/json" \
--data '{"name": "example-service-account-name"}' \
-- "${HDX_HYDROLIX_URL}/config/v1/service_accounts/"
{
"uuid": "43f50883-2d96-4faf-acb2-ca1b57faa667",
"audit": true,
"is_service_account": true,
"name": "example-service-account-name"
}
Assign roles with API
The endpoint Add roles to user requires the account UUID in the path and a list of roles in the POST body.
curl --fail \
--request POST \
--header "authorization: Bearer ${HDX_TOKEN}" \
--header "content-type: application/json" \
--data '{"roles": ["read_only"]}' \
-- "${HDX_HYDROLIX_URL}/config/v1/users/${HDX_SA_UUID}/add_roles/"
{
"success": true,
"message": "1 roles added to service account 43f50883-2d96-4faf-acb2-ca1b57faa667"
}
Generate token with API
The endpoint Generate service account tokens requires the account UUID in the path and supports an optional expiry date-time.
curl --fail \
--request POST \
--header "authorization: Bearer ${HDX_TOKEN}" \
--header "content-type: application/json" \
--data '{"expiry": "2025-08-21T14:44:09,428Z"}' \
-- "${HDX_HYDROLIX_URL}/config/v1/service_accounts/${HDX_SA_UUID}/tokens/"
The optional expiry field must be a valid ISO-8601 formatted datetime at any granularity. The example shows a fully specified Zulu timestamp, but the API will also accept 2025-08-21.
There are no other constraints on the expiry value, allowing creation of very long-lived tokens.
{
"token": "eyJhbGciOiJFZERTQSIsInR5cCI6IkpXVCJ9.eyJpc3MiOiJodHRwczovL2RvY3Mtc2FuZGJveC5oeWRyb2xpeC5kZXYvY29uZmlnIiwiYXVkIjoiY29uZmlnLWFwaSIsInN1YiI6IjQzZjUwODgzLTJkOTYtNGZhZi1hY2IyLWNhMWI1N2ZhYTY2NyIsImlhdCI6MTc1NTE4Mjg5OC4yNDI3MDgsImV4cCI6MTc1NTc4NzQ0OS40MjgsImp0aSI6IjMifQ.hUxapK08KdljtINmPTWeCBtx2gZrbJVmmU1zcg_RaaxMf5FQOGL02Vwf34-SNCdBJgZl1KJTjsgF-INOi1SIAQ"
}
Revoke tokens with API
The endpoint Invalidate service account tokens revokes all tokens associated with the service account.
curl --fail \
--request DELETE \
--header "authorization: Bearer ${HDX_TOKEN}" \
--header "content-type: application/json" \
-- "${HDX_HYDROLIX_URL}/config/v1/service_accounts/${HDX_SA_UUID}/tokens/"
Upon success, the server returns HTTP status code 204 and no content.
Delete with API
The endpoint Delete service account removes the service account.
curl --fail \
--request DELETE \
--header "authorization: Bearer ${HDX_TOKEN}" \
--header "content-type: application/json" \
-- "${HDX_HYDROLIX_URL}/config/v1/service_accounts/${HDX_SA_UUID}/"
Upon success, the server returns HTTP status code 204 and no content.
Verification steps
Verify the token is honored by using the Return information about the authenticated user endpoint. This endpoint reports information for the account linked to the token.
Other examples on this page show the user creating the service account and its tokens which are steps that require a user auth token.
In this step, test with a service account token.
curl --fail \
--header "authorization: Bearer ${HDX_SERVICE_TOKEN}" \
--header "content-type: application/json" \
-- "${HDX_HYDROLIX_URL}/config/v1/users/current/"
{
"uuid": "43f50883-2d96-4faf-acb2-ca1b57faa667",
"orgs": [],
"is_superuser": false,
"roles": [
"read_only"
],
"audit": true,
"emailVerified": false,
"enabled": true,
"is_service_account": true,
"name": "example-service-account-name"
}
Troubleshooting
- Service accounts feature are supported in v5.4 and above. Verify the cluster is running v5.4 or higher.
- Ensure that the user attempting to manage service accounts has the required permissions.
- Ensure that the service account has appropriate permissions. Access is enforced at time of use, so changing roles assigned to an account can be tested without changing an existing token.
Related material
Updated 3 months ago